We Are At War... A Cyber War; With 20 Billion Connected Devices. Just How Safe Do You Feel?
The following is an overview of the cyber-security threat landscape, how connected devices are resulting in us becoming digitalised versions of ourselves and how this explosion impacts the healthcare industry.
In my next article, I will talk about what needs to be done in order to secure healthcare, the difficulties associated with this and how McKesson are poised at the forefront of innovation in an attempt to tackle these challenges.
Cyber Security Breaches Are Now A Daily Occurrence
So if I was to start by asking for a show of hands from anyone who has ever received an email saying that they have won a sum of money (e.g. a lottery) and all they need to do is send bank details in order for the money to be transferred, the majority of people would most likely raise their hands. That is because these types of techniques have become a very common way for attackers to try and obtain your personal information; and unfortunately, these type of scams are now becoming a daily occurrence.
But it's not only individuals who should remain vigilant, it's also multi-billion dollar companies. To gain access into an organisation's network, hackers use a range of techniques such as exploiting weaknesses in software applications, infecting mobile applications and social engineering. When large organisations fall victim to these scams, large financial costs can be incurred due to compromised data, inaccessible services and brand/reputation damages (Smartech, 2015). To see how common these types of attacks has become, you only have to look through the news over the past few months to see data breaches within Facebook, Eir, Ticketmaster and Dixons (The Journal, 2018).
Figure 1: Cyber Security Breaches Are Now A Daily Occurrence
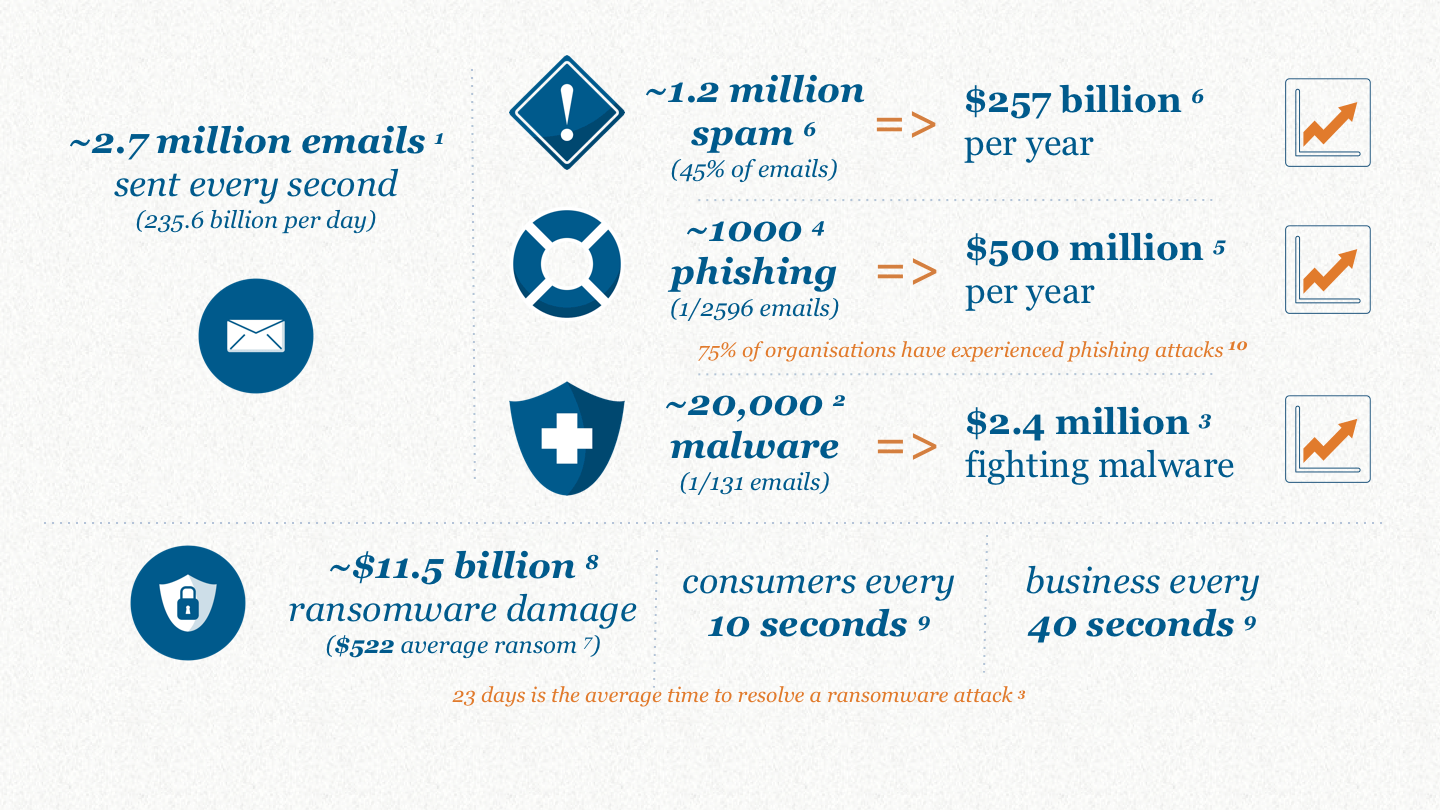
Threat Statistics
Figure 2: Threat Statistics
So if we take a look into email threat statistics, the most direct vehicle for transmitting these scams, it’s clear to see the reason why they are so common and why we constantly need to remain vigilant. There are 235.6 billion emails sent every day, equating to approximately 2.7 million emails sent every single second (Threat Statistics 1).
From the 2.7 million emails that are sent every second, 45% are spam, equating to 1.2 million spam emails sent every single second, costing companies $257 billion per year (Threat Statistics 6).
From the 2.7 million emails that are sent every second, 1 in every 2596 of these are phishing, equating to 1000 phishing emails sent every single second (Threat Statistics 4), costing American businesses $500 million worth in damages per year (Threat Statistics 5). A staggering 75% of organisations have reported experiencing these type of phishing attacks (Threat Statistics 10).
From the 2.7 million emails that are sent every second, 1 in every 131 of these are malware, equating to 20,000 malware emails sent every single second (Threat Statistics 2), resulting in companies spending an average of $2.4 million per year trying to protect themselves (Threat Statistics 3).
For these malware attempts that has been successful, computers and mobile devices are left infected, often restricting access to files and threatening permanent data destruction unless a ransom is paid. It is estimated that the global ransomware damage costs will hit $11.5 billion by 2019 (Threat Statistics 8), with an average ransom of $522 (Threat Statistics 7). It is reported that consumers are attacked every 10 seconds by ransomware and businesses every 40 seconds (Threat Statistics 9) with an average of 23 days to resolve these attacks (Threat Statistics 3).
The Phishing Footballer
In one of my previous articles, The Phishing Footballer, I outlined the dangers of phishing regardless of the industry you work in, by giving an example of a football club who were tricked into paying €2 million into a cyber criminals account as part of a transaction for the transfer of one of their players. An example to show that opportunists are fast to take advantage of any major events or global issues that are trending and why everyone must remain vigilant at all times.
Figure 3: The Phishing Footballer
Is Leonardo da Vinci To Blame?
In another one of my previous articles, Why You Should Thank Leonardo da Vinci - An Overview of User Experience (UX) Design, I took a look at how the origin of User Experience (UX) dates back to Leonardo da Vinci. As people are becoming more familiar with the dangers of spam and phishing emails, and therefore becoming more vigilant in identifying such threats, UX has started to play a huge role in the success and adoption of these type of threats. In recent times, cyber criminals have started incorporating modern UX design and communication principles into their tactics by designing attacks that match corporate or well known templates to trick users into clicking their links and ads.
Figure 4: Why You Should Thank Leonardo da Vinci
20 Billion Connected Devices
The reality is that devices are starting to infiltrate our personal and professional lives at an explosive rate. We are now living in an era where it's possible to reach millions, if not billions of people with a single click of a button. There are now currently more monthly users on Facebook (Zephoria, 2018) than the population of the world in 1940 (WorldOMeters, 2018). In this ever growing expansion of connected nodes, it is estimated that by 2020, there will be over 20 billion connected devices (Gartner, 2017), with a market value of over $450 billion (Forbes, 2017a). These devices that we accept into our homes for our enjoyment and to make our lives better, are increasing our vulnerability to cyber-security threats as each one of these devices act as a portal into your personal network, and each device is making it easier and more attractive for attackers.
Figure 5: 20 Billion Connected Devices
The Digital Human
But it’s not only the devices that are becoming more and more connected to each other, we are also becoming more and more connected to our devices. We are essentially becoming digitalised versions of ourselves; and as our digital footprint and global connectivity increases, the opportunities also rise for attackers to infiltrate and exploit weaknesses in our ever growing network of connections.
Figure 7: The Digital Human
The reliance we place on technology is now bigger than ever. In 2017, China lead the way in moving towards a cashless economy by reaching almost $13 trillion in mobile transactions (South China Morning Post, 2018). If you look at the issue that Ulster Bank had back in April of this year, whereby transactions and lodgements disappeared from peoples accounts for a short period of time (Silicon Republic, 2018), it's scary to think that as we move further towards technology advancements, that our whole digital life could potentially be wiped out without warning.
Figure 8: Mattress Banking
And if this is a possibility, maybe we should move back to storing money under our mattresses again. In 2017, a survey actually showed that almost 10% of people in Great Britain hide money under their beds (Express, 2017).
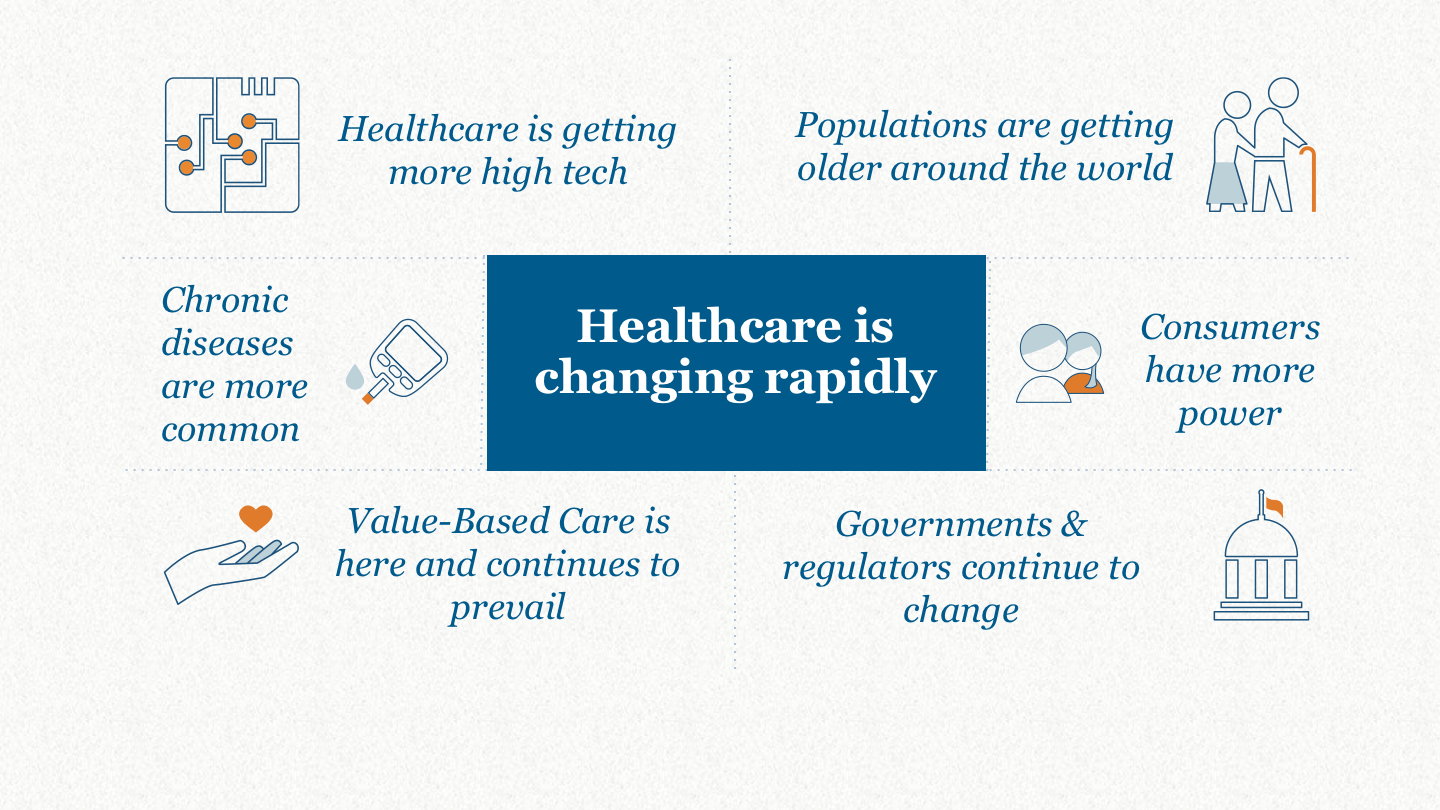
Healthcare Landscape
Now let us look at how this impacts the healthcare industry. The healthcare industry is currently experiencing an era of unprecedented change, largely due to advancements in technology and a rising demand for healthcare services. This continuous growth of innovation is paving the way for new opportunities, but also creating a lot of challenges for healthcare and the economy. A primary driver is the ongoing shift in global demographics resulting in people living longer lives across the globe. There are now more than 656 million people over the age of 65 (Deloitte, 2018) and in Ireland alone, the percentage of the population aged 65 or over grew by 19.1% between 2011 and 2016 (CSO, 2016). Now people living longer lives sounds great, but unfortunately, we haven’t quite got to the stage yet where the infrastructure is able to handle this extra demand, resulting in a higher rate of medical conditions and chronic diseases that are more prevalent in older people, such as arthritis, lung/heart illnesses and diabetes. Diabetes is actually expected to rise to over 642 million people by 2040 as a result of rapid urbanisation, sedentary lifestyles, changing diets and rising obesity levels (Deloitte, 2018). To tackle these conditions, consumers are now in a greater position of power in terms of choosing a healthcare plan that best suits their needs. Data plays an important role in these decisions as consumers are now provided with a plethora of information regarding providers, care options, outcomes and cost. People are also more open to share more and more information about themselves with the premise that they will receive higher value based care.
Figure 9: Healthcare Landscape
Digital Health
As a result, we are now seeing an explosion in cloud-based data due to the growth of electronic health records and patient portals becoming standard in the industry. Hospitals and experts are beginning to take advantage of these mediums in order to share their expert knowledge and collaborate together to solve tough challenges. But this shift towards online, again give attackers an opportunity to tackle a new market. It is reported that the healthcare industry experiences twice as many attacks as other industries (CSO, 2018) and that over 90% of hospitals say they’ve reported a data breach in the last two years. These data breaches in the U.S. are costing the healthcare industry $6.2 billion each year, with an average of $3.7 million with a high of $113 million per organisation (Beckers Hospital Review, 2017). Consequently, ensuring the security and privacy of consumer data is a critical priority for the healthcare industry.
Figure 10: Digital Health
Why Is Healthcare Data So Valuable?
But the healthcare industry is slower than most industries when it comes to updating their cyber-security. This is mainly due to the increase in IoT devices and the number of endpoints that need to be secured (The SSL Store, 2018). As hospitals continue their plans to spend on technology, for example, India are expecting to spend over $200 billion on hospital infrastructure by 2024 (Deloitte, 2018), these numbers are estimated to keep on rising. But the main reason of why the healthcare industry is so heavily attacked, lies in the value of healthcare records.
The wealth of personal information contained within healthcare records is more highly sought after than that of credit card information. Credit card information has a limited shelf life and can only be used while the card is unblocked. Medical record information can be easily be monetised as it has a much broader utility and can be used to commit multiple types of fraud and identity theft. It's important to note here that the main value placed on medical card date is due to the fact that even when the compromise is discovered, the data doesn't change (i.e. your medical history will also be your medical history). It is said that credit card information can be sold for $1-$2 whereas medical records can be sold for up to $100 on the underground cybercrime networks. The medical records of children are especially lucrative on the black market, since the theft likely goes undetected until the child turns 18. Probably the scariest affect is when medical identification theft is used to obtain medical care. As a result, the victim can no longer trust that his/her medical information is safe or that they are receiving accurate medical care (Ingram, 2017). If you compare credit card fraud against medical record breaches, you will find that in 2016, there was over 1.5 million U.S. consumer credit card complaints related to fraud and over 27 million medical record breaches, representing almost 10% of the U.S. population (Forbes, 2017b).
Stay tuned for my next article, I will talk about what needs to be done in order to secure healthcare, the difficulties associated with this and how McKesson are poised at the forefront of innovation in an attempt to tackle these challenges.
Figure 11: Why Is Healthcare Data So Valuable
References
- Beckers Hospital Review. (2017). Healthcare breaches cost $6.2B annually. [online] Available at: https://www.beckershospitalreview.com/healthcare-information-technology/healthcare-breaches-cost-6-2b-annually.html
- CSO. (2016). Census of Population 2016 - Profile 3 An Age Profile of Ireland. [online] Available at: https://www.cso.ie/en/releasesandpublications/ep/p-cp3oy/cp3/agr/
- CSO. (2018). Healthcare Experiences Twice the Number of Cyber Attacks As Other Industries. [online] Available at: https://www.csoonline.com/article/3260191/security/healthcare-experiences-twice-the-number-of-cyber-attacks-as-other-industries.html
- Deloitte. (2018). 2018 Global health care outlook - The evolution of smart health care. [online] Available at: https://www2.deloitte.com/global/en/pages/life-sciences-and-healthcare/articles/global-health-care-sector-outlook.html
- Express. (2017). Hidden loot: You wont believe the number of Britons that hide CASH under their bed. [online] Available at: https://www.express.co.uk/finance/personalfinance/804732/British-people-money-savings-stash-cash-hidden-mattress-survey
- Figure Cover: We Are At War. https://thefinanser.com/wp-content/uploads/2017/09/Digital-Human.jpg
- Figure 1: Cyber Security Breaches Are Now A Daily Occurrence. https://d2v9y0dukr6mq2.cloudfront.net/video/thumbnail/1809Tdj/videoblocks-close-up-shot-of-a-masked-hacker-in-a-hoodie-standing-in-the-middle-of-data-center-full-of-rack-servers-and-hacking-it-with-his-notebook-shot-on-red-epic-w-8k-helium-cinema-camera_h9f4rilhe_thumbnail-full01.png
- Figure 3: The Phishing Footballer. https://i1.mdzol.com/files/image/672/672634/56f5c40d4cec1__1240!.jpg
- Figure 4: Da Vinci Kitchen Nightmare. https://s-media-cache-ak0.pinimg.com/736x/c2/8a/3c/c28a3c5b1323c5617414a5fadfba2c01.jpg
- Figure 5: 20 Billion Connected Devices. https://pc-tablet.com/wp-content/uploads/2017/11/IoT-Smarthome.jpg
- Figure 7: The Digital Human. http://cognitiveworld.com/article/emergence-cognitive-digital-physical-twins-cdpt-21st-century-icons-and-beacons
- Figure 8: Mattress Banking. http://rdcnewscdn.realtor.com/wp-content/uploads/2016/09/money-under-mattress.jpg
- Figure 10: Digital Health. https://m.care/wp-content/uploads/2017/09/bigstock-healthcare-people-technology-174291787.jpg
- Figure 11: Why Is Healthcare Data So Valuable. https://mir-s3-cdn-cf.behance.net/project_modules/max_1200/66dd6915208173.587f6a002dce4.jpg
- Forbes. (2017a). 2017 Roundup Of Internet of Things Forecasts. [online] Available at:https://www.forbes.com/sites/louiscolumbus/2017/12/10/2017-roundup-of-internet-of-things-forecasts/
- Forbes. (2017b). The Real Threat Of Identity Theft Is In Your Medical Records, Not Credit Card. [online] Available at: https://www.forbes.com/sites/forbestechcouncil/2017/12/15/the-real-threat-of-identity-theft-is-in-your-medical-records-not-credit-cards/#6423ec001b59
- Gartner. (2017). Leading the IoT: Gartner Insights on How to Lead in a Connected World. [online] Available at: https://www.gartner.com/imagesrv/books/iot/iotEbook_digital.pdf
- Ingram Micro Professional & Training Services. (2017). Cybersecurity in Healthcare. [online] Available at: https://www.youtube.com/watch?v=p-FPIZlgQkg
- Silicon Republic. (2018). Ulster Bank is investigating widespread reports of accounts missing funds. [online] Available at: https://www.siliconrepublic.com/enterprise/ulster-bank-issue
- Smarttech. (2015). Cyber Security for Healthcare Organisations - Smarttech & IBM. [online] Available at: https://www.youtube.com/watch?v=95eC1HoUKPI
- South China Morning Post. (2018). China pulls further ahead of US in mobile payments with record US$12.8 trillion in transactions. [online] Available at: http://www.scmp.com/tech/apps-gaming/article/2134011/china-pulls-further-ahead-us-mobile-payments-record-us128-trillion
- The SSL Store. (2018). The Healthcare Industry is lagging behind on Cybersecurity. [online] Available at: https://www.thesslstore.com/blog/healthcare-industry-cybersecurity-2018/
- The Journal. (2018). Data Breach News. [online] Available at: http://www.thejournal.ie/data-breach/news/
- Threat Statistics 1: http://radicati.com/wp/wp-content/uploads/2015/02/Email-Statistics-Report-2015-2019-Executive-Summary.pdf
- Threat Statistics 2: https://blog.barkly.com/phishing-statistics-2017
- Threat Statistics 3: https://www.accenture.com/t20170926T072837Z__w__/us-en/_acnmedia/PDF-61/Accenture-2017-CostCyberCrimeStudy.pdf
- Threat Statistics 4: https://blog.campaignmaster.co.uk/2017/10/05/how-to-avoid-email-phishing/
- Threat Statistics 5: https://www.forbes.com/sites/leemathews/2017/05/05/phishing-scams-cost-american-businesses-half-a-billion-dollars-a-year/#3a9d2c423fa1
- Threat Statistics 6: https://www.propellercrm.com/blog/email-spam-statistics
- Threat Statistics 7: http://images.mktgassets.symantec.com/Web/Symantec/%7B3a70beb8-c55d-4516-98ed-1d0818a42661%7D_ISTR23_Main-FINAL-APR10.pdf?aid=elq_
- Threat Statistics 8: https://cybersecurityventures.com/ransomware-damage-report-2017-part-2/
- Threat Statistics 9: https://blog.barkly.com/new-ransomware-trends-2017
- Threat Statistics 10: https://www.tripwire.com/state-of-security/security-data-protection/three-quarters-organizations-experienced-phishing-attacks-2017-report-uncovers/
- WorldOMeters. (2018). World Population by Year. [online] Available at. http://www.worldometers.info/world-population/world-population-by-year/
- Zephoria. (2018). The Top 20 Valuable Facebook Statistics. [online] Available at. https://zephoria.com/top-15-valuable-facebook-statistics/